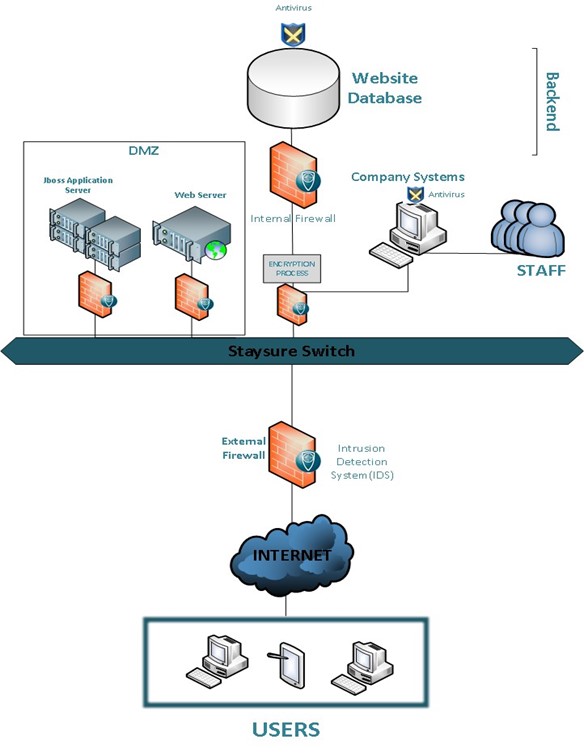
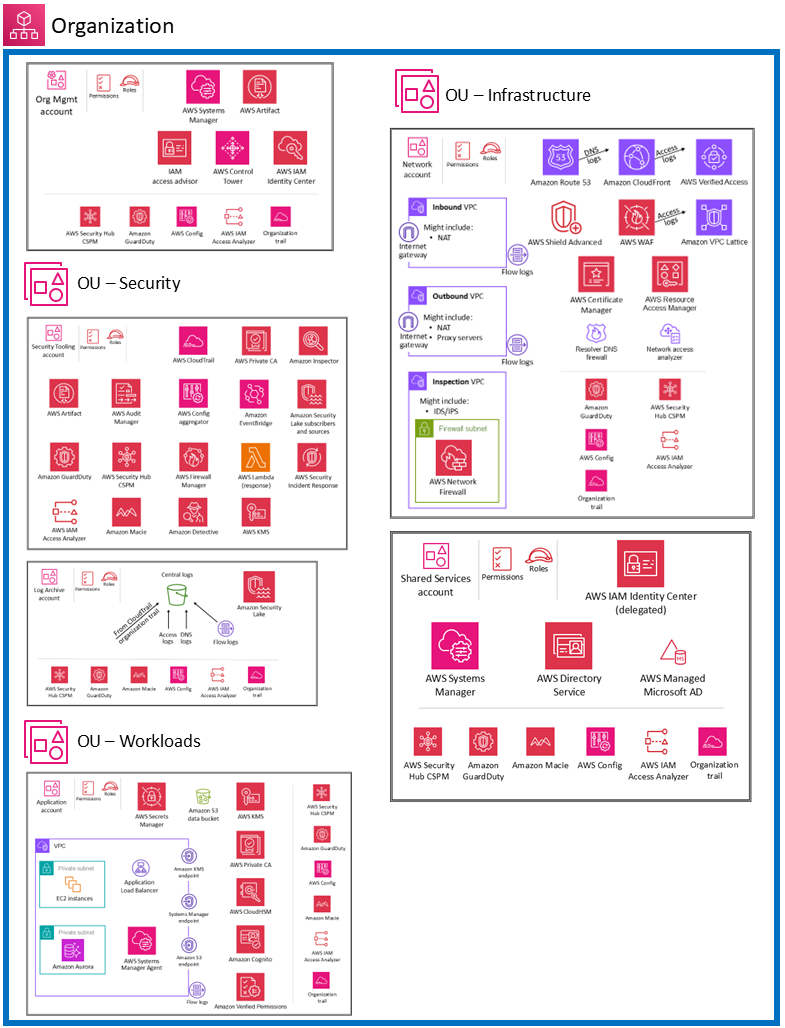
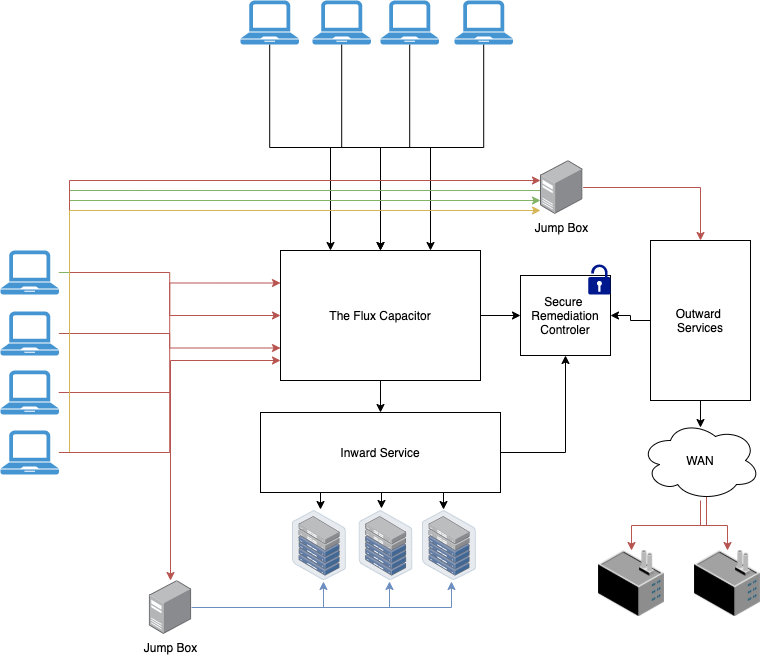
42 security architecture diagram
Client Server Architecture: Diagram, Types, Examples, Components Client-server architecture is a shared computer network architecture where several clients (remote system) send many requests and finally to obtained services from the centralized server machine... How to Draw Useful Technical Architecture Diagrams | Medium A technical architecture diagram provides a bird's eye view of the infrastructure of your Usually, a digital solution architect will draft out high-level architecture diagrams to facilitate technology...
Microsoft Cybersecurity Reference Architectures - Security... The diagrams describe how Microsoft security capabilities integrate with Microsoft platforms and The reference architectures are primarily composed of detailed technical diagrams on Microsoft...

Security architecture diagram
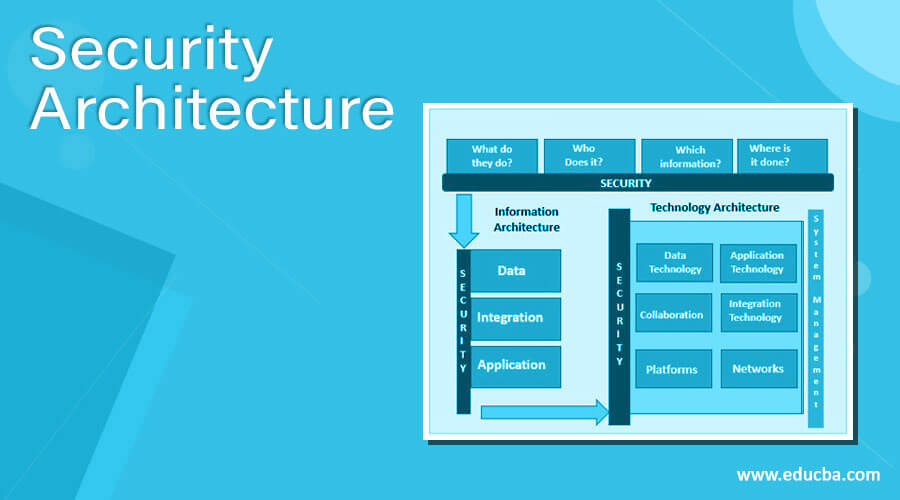
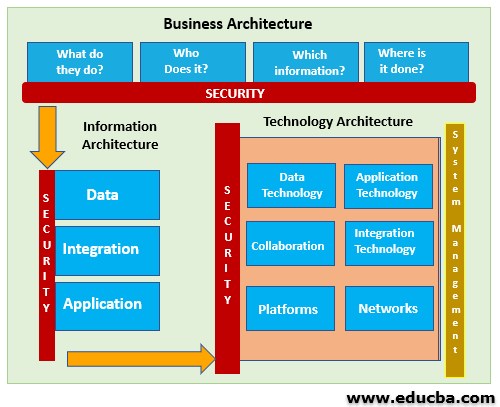
Enterprise information security architecture - Wikipedia Enterprise information security architecture (ZBI) is a part of enterprise architecture focusing on information security throughout the enterprise. The name implies a difference that may not exist between small/medium-sized businesses and larger organizations. Enterprise Information Security Architecture: What... | RSI Security Enterprise Information Security Architectures (EISAs) are fundamental concepts or properties of a EISA applications, software inventories, and diagrams should also be included in these charts to... PDF Microsoft Word - Architectural Approach to Information Security... Oracle White Paper— Information Security: A Conceptual Architecture Approach. The diagram in Figure 2 represents a conceptual model for the way that we view Information Security.
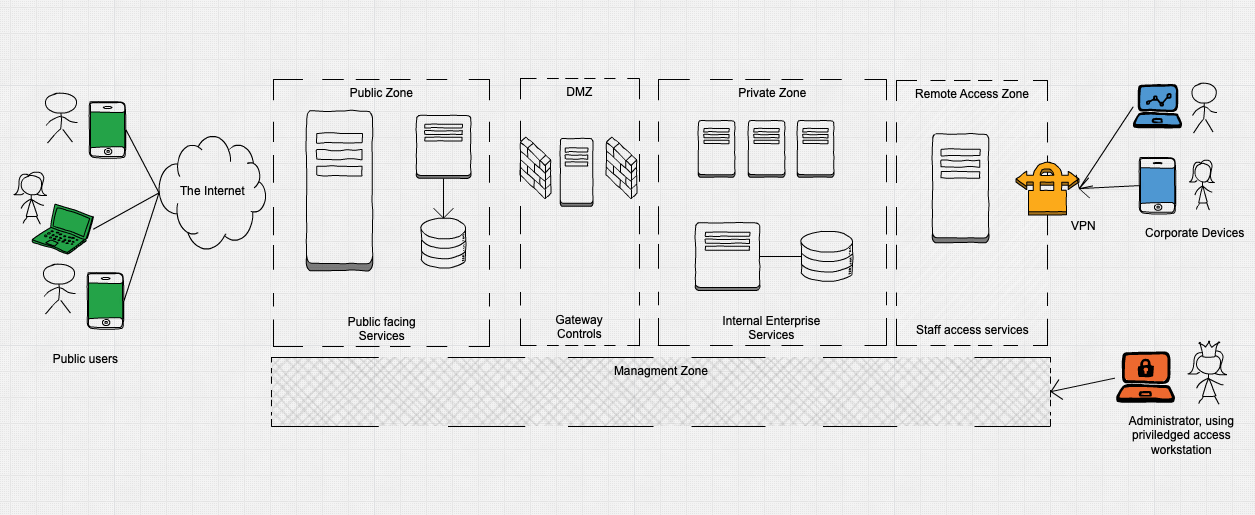
Security architecture diagram. Cloud Computing System Architecture Diagrams Security - For MultiCloud system architectures, it's important to realize that The architecture diagrams below show a progression from simple to more complex reference architectures. Cloud Security Research for Enterprise Architecture Cloud security architecture helps cloud providers develop industry-recommended, secure and interoperable identity, access and compliance management configurations, and practices. Software Development Templates & Examples | Miro Manage network architectures and map out systems with Miro's Software Development templates. Create one shared understanding and improve collaboration. Security Architecture with Diagram Security architecture is defined as the architectural design that includes all the threats and potential risks which can be In the above diagram, the high-level design of the system architecture is shown.
AWS Architecture Icons | Drawing and diagramming tools Architecture diagrams are a great way to communicate your design, deployment, and topology. On this page you will find an official collection of AWS Architecture Icons (formerly Simple Icons) that... PDF Security Architecture The Security Architecture & Design domain contains the concepts, principles, structures, and standards used to design, implement, monitor, and secure, operating systems, equipment, network... (PDF) Enterprise Architecture & Security Architecture Development to the security, Security Architecture concept was created. The architectural approach can. help enterprises classify main elements of information security from different points of. What is Security Architecture? - Definition from Techopedia Form: Security architecture is associated with IT architecture; however, it may take a variety of forms. It generally includes a catalog of conventional controls in addition to relationship diagrams...
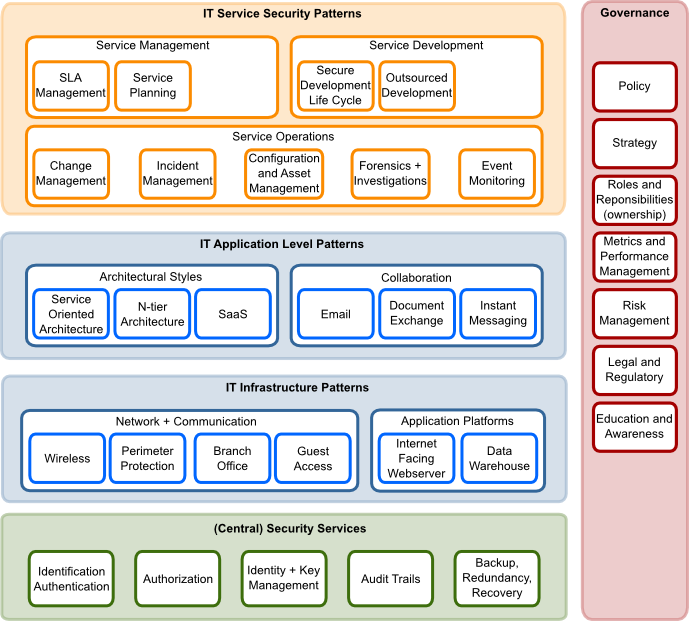
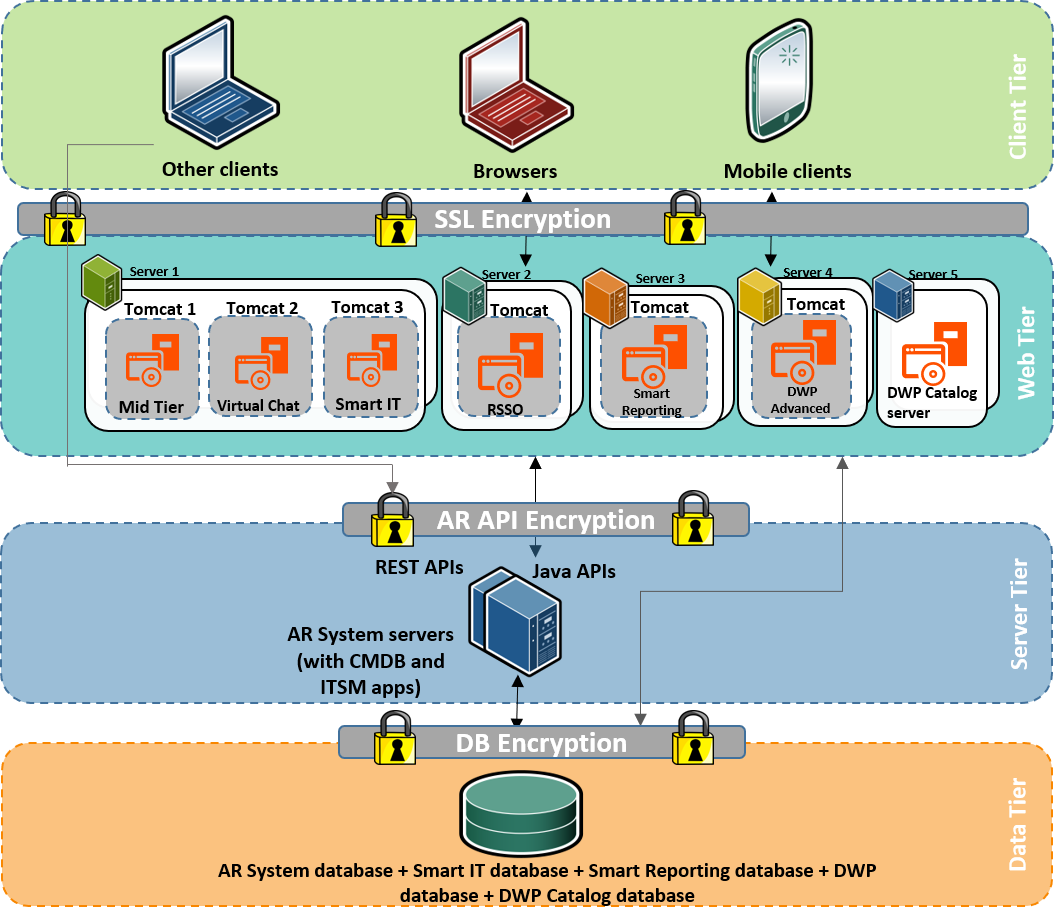
Security Architecture - an overview | ScienceDirect Topics Security Architecture and Design describes fundamental logical hardware, operating system, and software security components and how to use those components to design, architect, and evaluate... Architecture page guidance — Security Guide documentation The architecture diagram shows the logical layout of the system so the security reviewers can step through the architecture with the project team. It is a logical diagram which shows how the... Architecture security features | Platform security - Arm Developer Platform security resources to help developers achieve PSA Certified on Arm-based platforms. All resources are designed for M- and A-profile IoT-devices and are developed and made freely available... Enterprise Security Architecture Resources - Cybersecurity Memo Enterprise Security Architecture (ESA) is a relatively new concept to most business & IT Following diagram is from Information Security Society Switzerland's paper "What is Security Architecture".
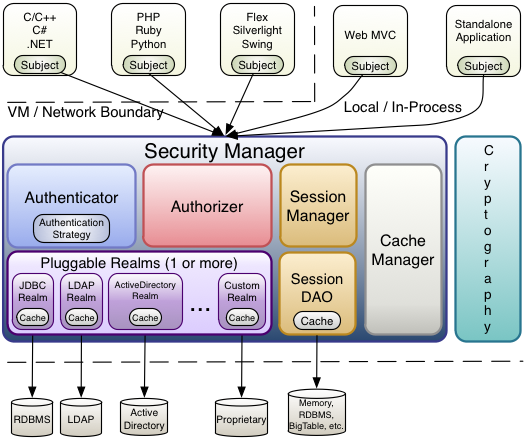
Spring security architecture diagram - W3schools Spring security architecture with diagram : Spring security is a flexible and powerful authentication and authorization framework to create secure J2EE-based Enterprise Applications.
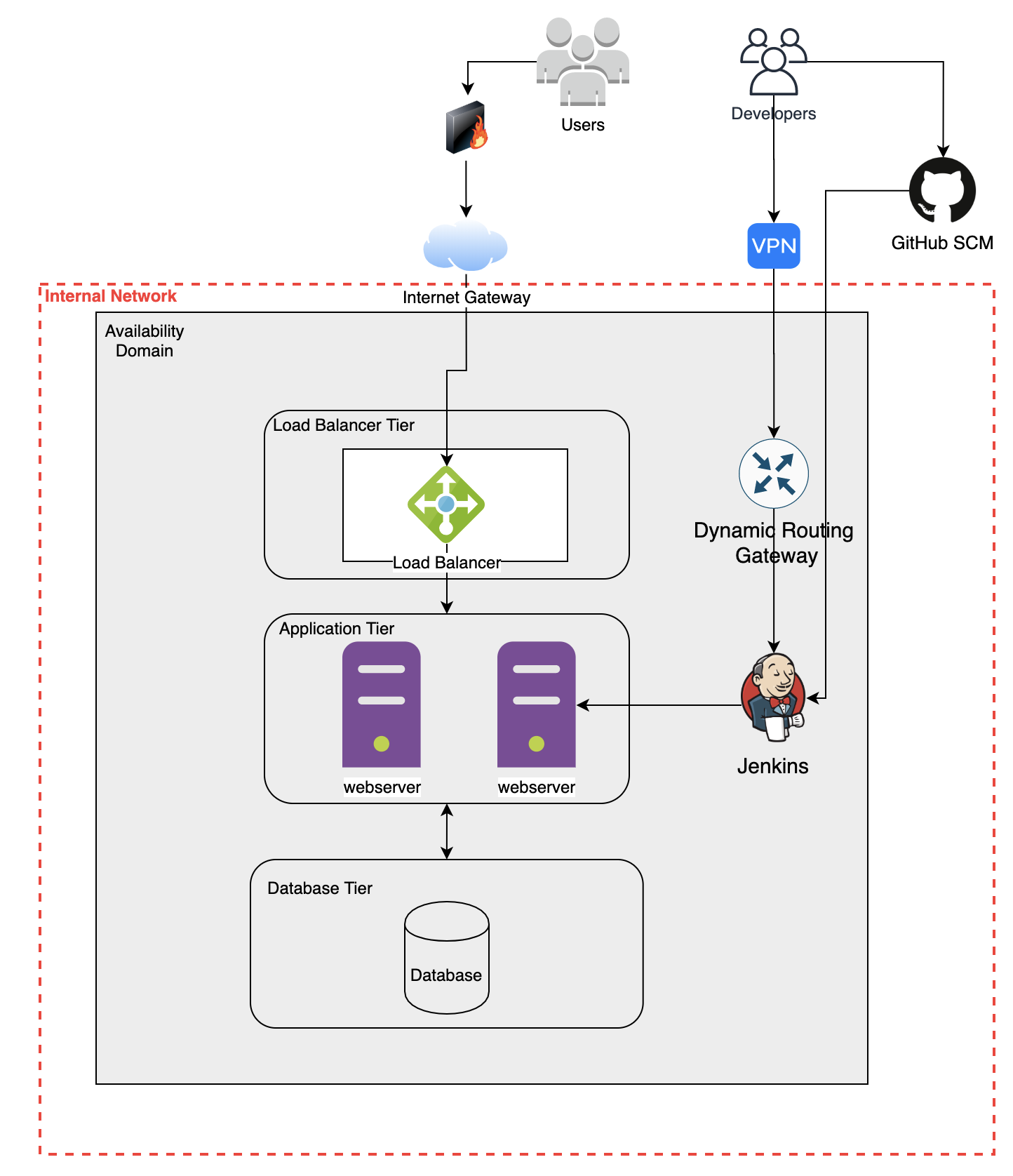
How to Quickly Design AWS Architecture Diagrams AWS architecture diagrams and templates to quickly draw diagrams. This AWS architecture diagram describes the configuration of security groups in Amazon VPC against reflection attacks...
security_architecture_diagram/folder.html at master... Coursework. Contribute to simonblund/security_architecture_diagram development by creating an account on GitHub.
PDF SASE Architecture Reference Guide Architecture Reference Guide for the Implementation of Secure Access Service Edge. This document provides a basic understanding of SASE architecture, explains how it solves different...
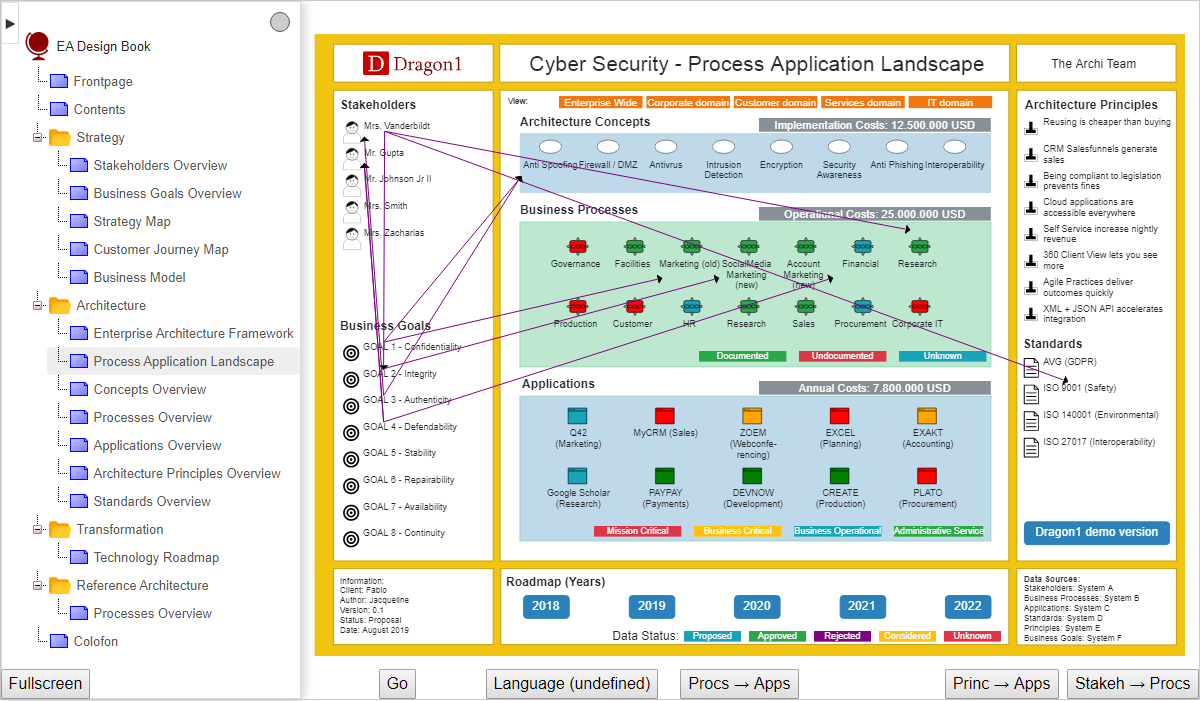
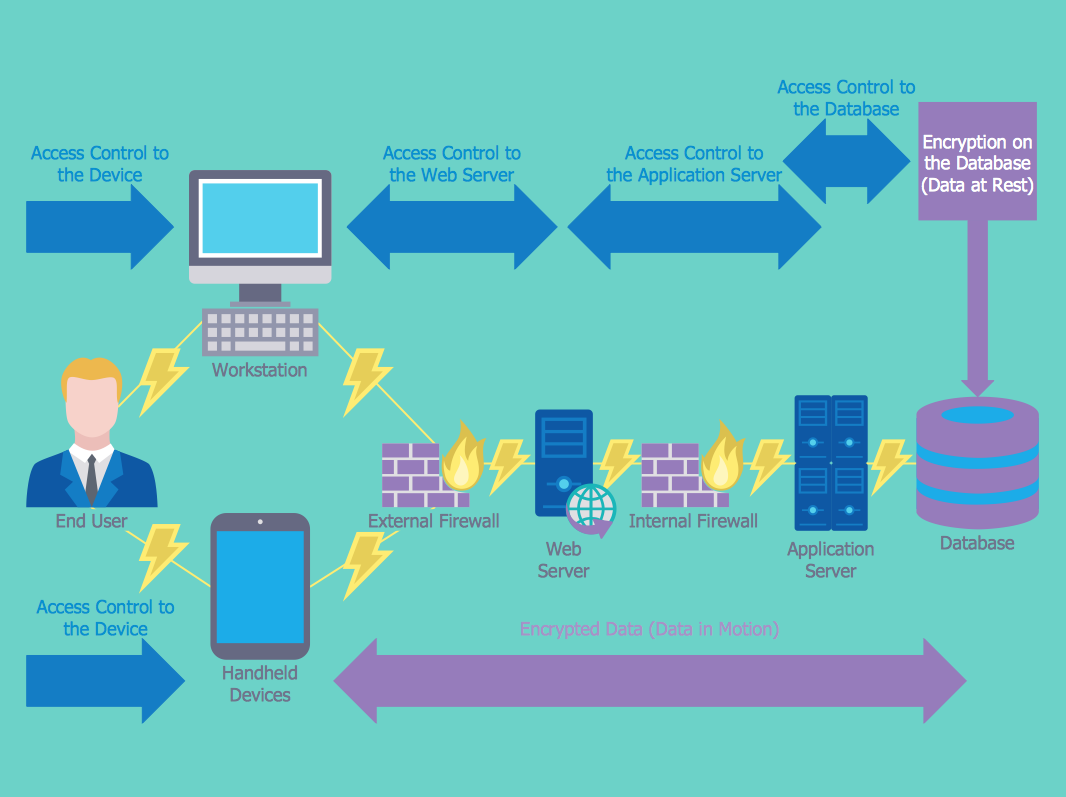
Network Security Architecture Diagram The Network Security Architecture Diagram samples you see on this page were created in ConceptDraw DIAGRAM using the predesigned objects from the libraries of Network Security...
How to Create Application Architecture Diagram Online? Terrastruct is a diagramming tool designed for software architecture. Unlike other diagramming tools that produce static images, Terrastruct lets you express the complexity of your software designs.
What is network security architecture diagram? - Search Network Security Architecture Diagram visually reflects the network's structure and construction, and all actions undertaken for ensuring the network security which can be executed with help of software...
Complete Guide to Architecture Diagrams - Edraw The architecture diagram examples serve various functions. It always helps the relevant users to The diagram shows security policies, management tools, business plans, teams, roles, interaction...
Free Online Architecture Diagram Maker | EdrawMax Online Effortlessly create architecture diagram online using EdrawMax online diagramming tool. Online data security has been a hot issue arising more attention nowadays, therefore, we sincerely promise...
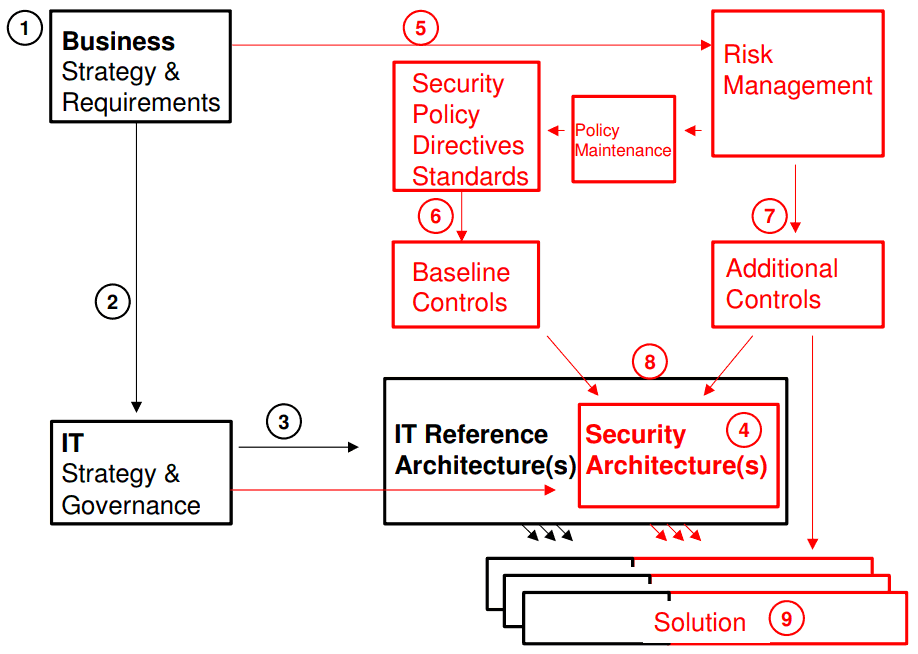
PDF Security Architecture Methodology for the Electric Sector, Version 2.0 A security architecture diagram may be one component of the cyber security risk assessment package that supports a cyber security risk strategy. A cyber security risk strategy is documented in...
What Is Security Architecture, and What Do You Need to... — dig8ital Security architecture is vital for modern businesses. Learn all about why a security architecture In the modern age of technology, the importance of securing your organization against cyber security...
PDF Microsoft Word - Architectural Approach to Information Security... Oracle White Paper— Information Security: A Conceptual Architecture Approach. The diagram in Figure 2 represents a conceptual model for the way that we view Information Security.
Enterprise Information Security Architecture: What... | RSI Security Enterprise Information Security Architectures (EISAs) are fundamental concepts or properties of a EISA applications, software inventories, and diagrams should also be included in these charts to...
Enterprise information security architecture - Wikipedia Enterprise information security architecture (ZBI) is a part of enterprise architecture focusing on information security throughout the enterprise. The name implies a difference that may not exist between small/medium-sized businesses and larger organizations.















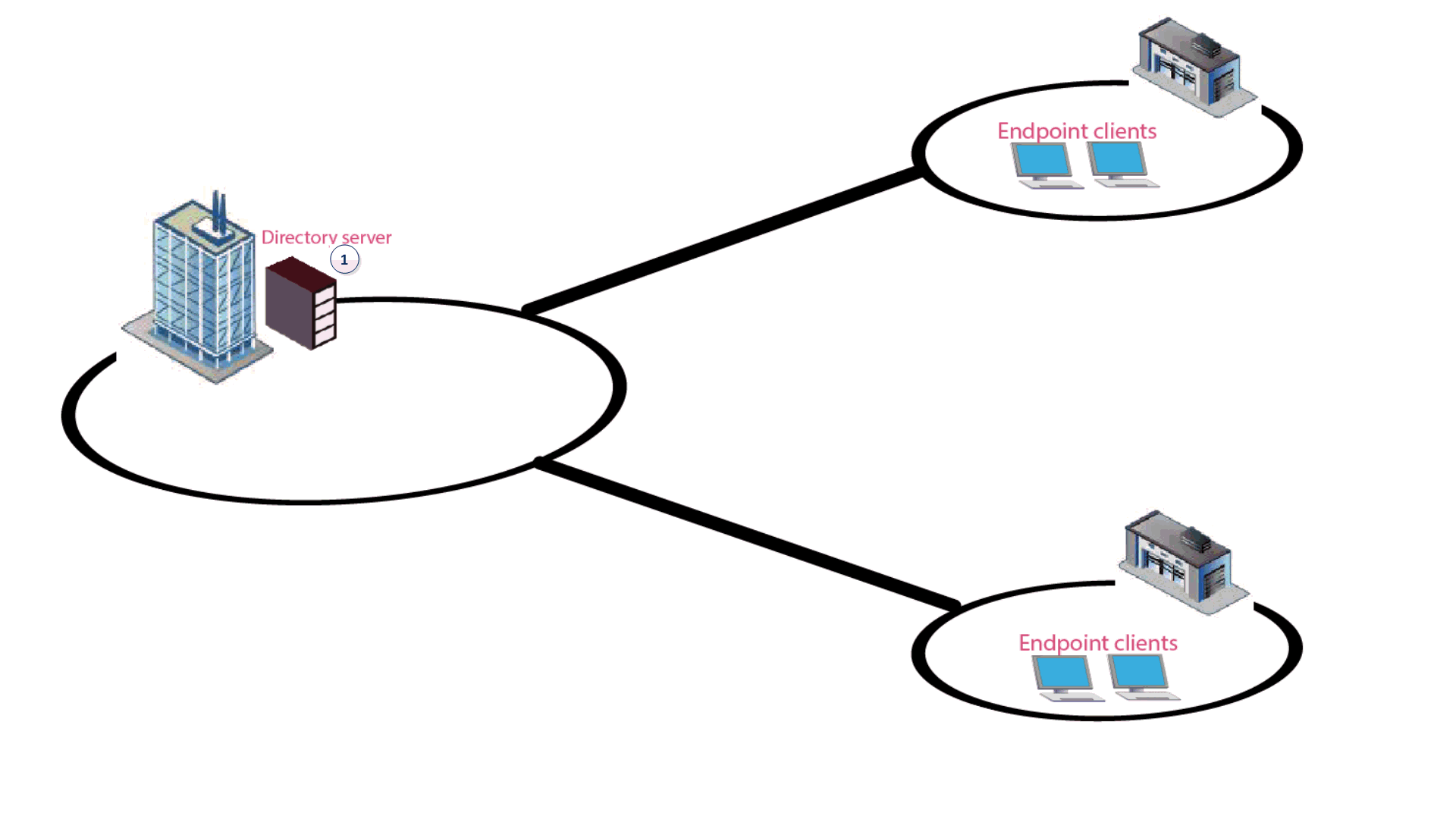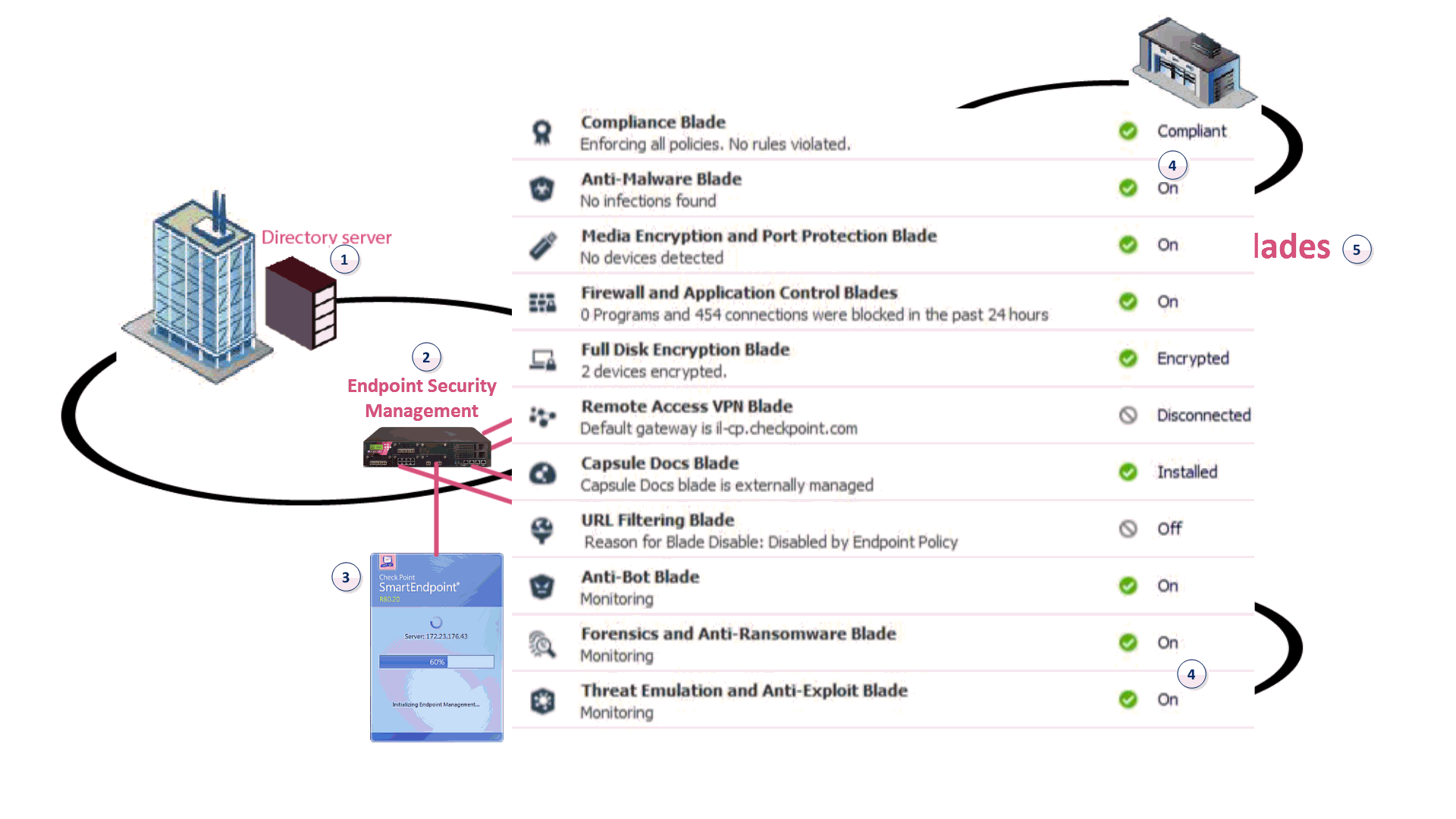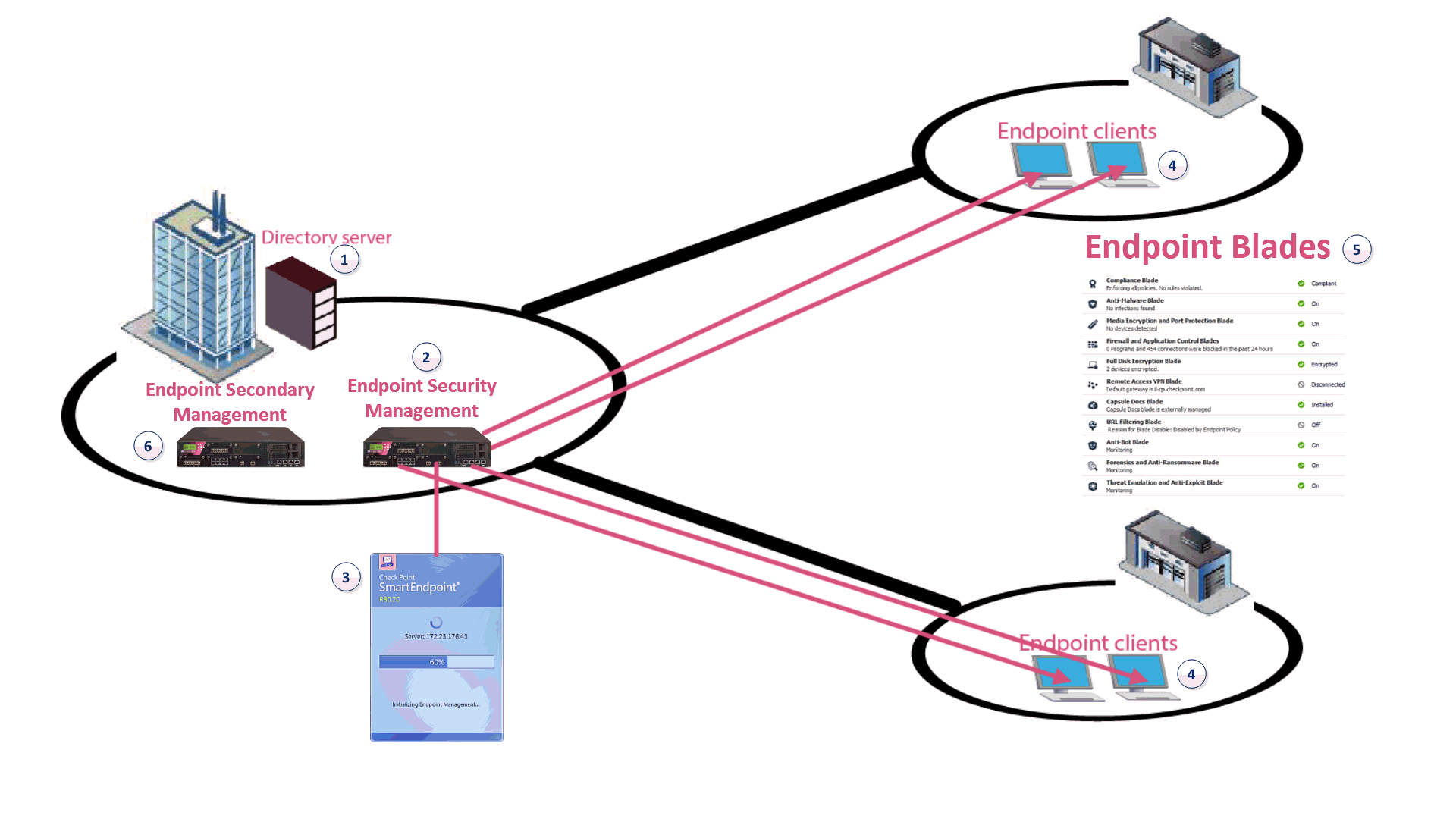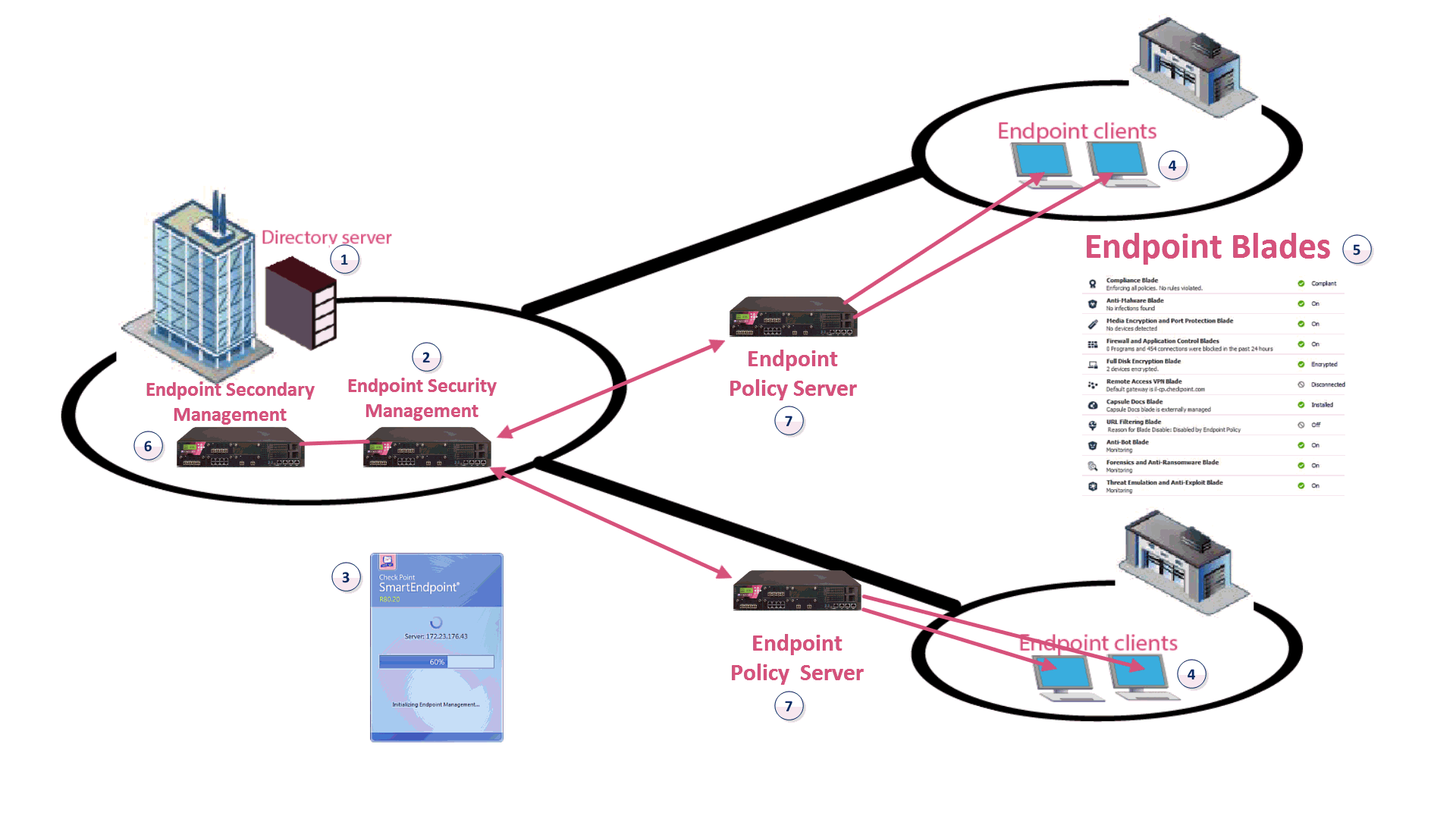



![PDF] A security architecture for data privacy and security ...](https://d3i71xaburhd42.cloudfront.net/40b9e63d84cd9afff76e015eb5f8e612e512a90b/2-Figure1-1.png)




Comments
Post a Comment